Poa&M Template Excel
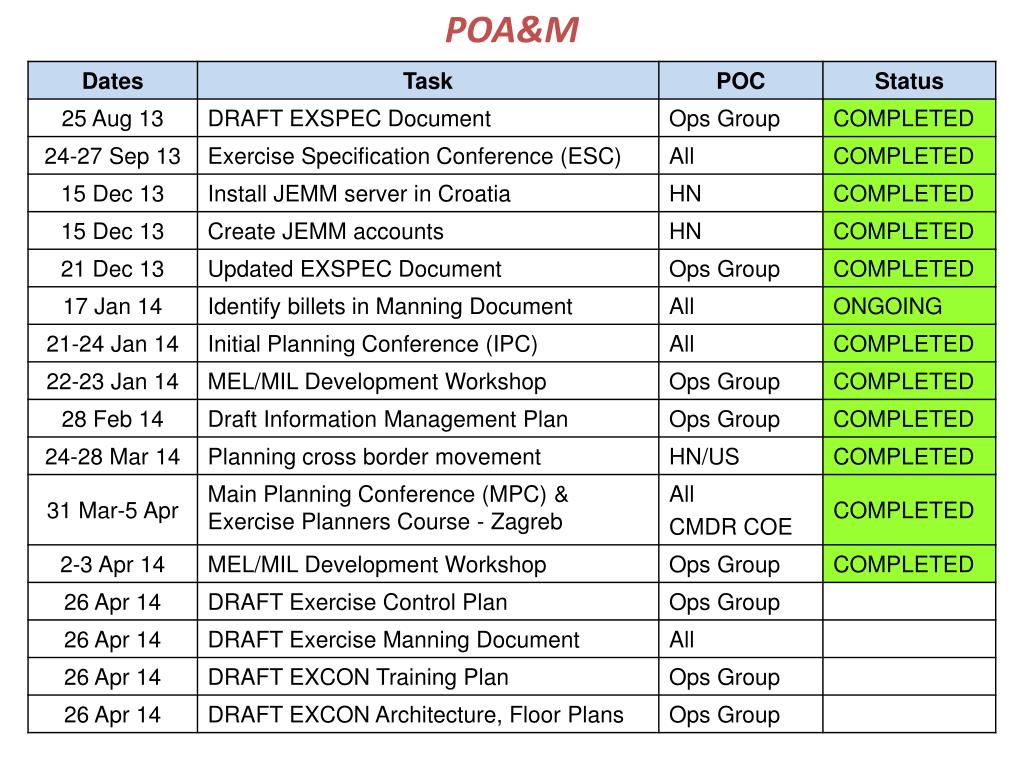
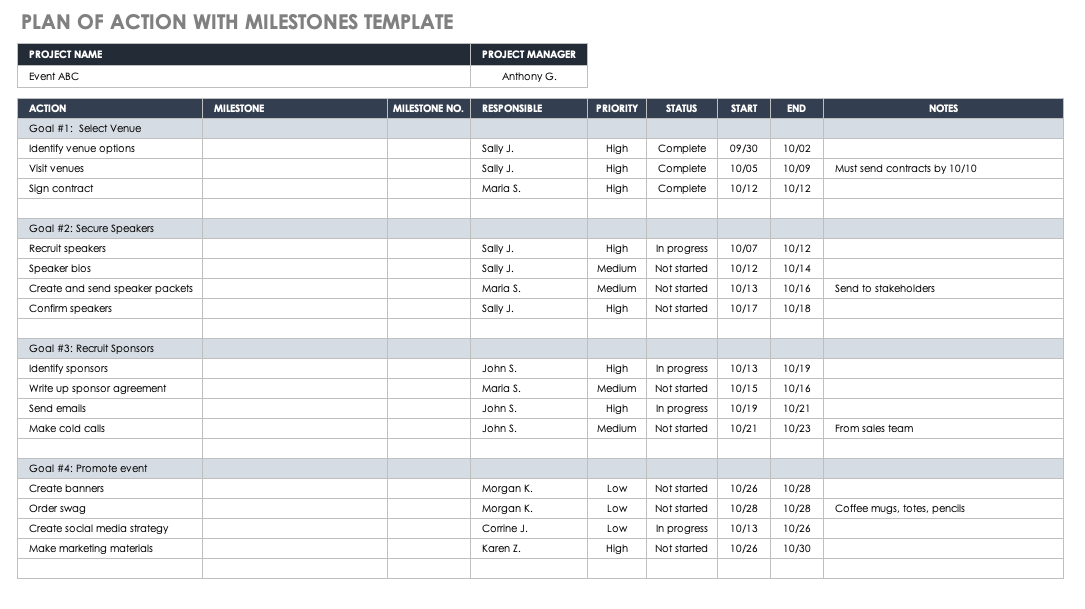
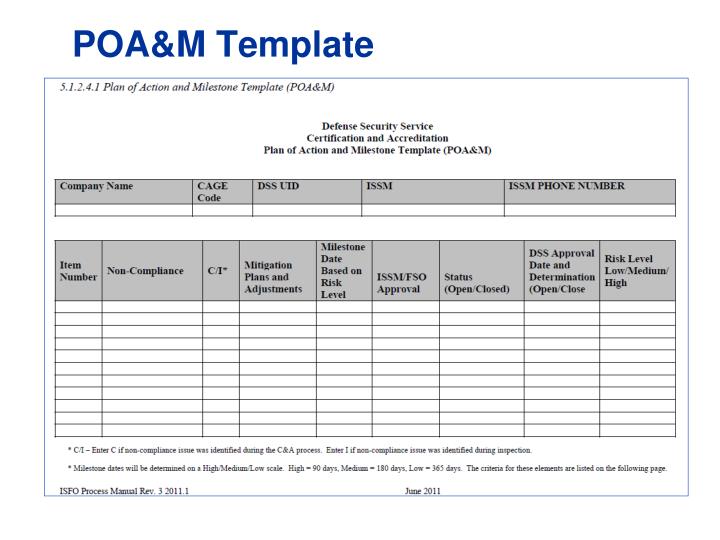
Poa&M Template Excel - Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf of the program office or the dod component. Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. The csp may add to the format, as necessary, to comply with its internal policies and fedramp requirements; Web the fedramp poa&m template provides the required information presentation format for preparing and maintaining a poa&m for the system. Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective action and implement/test the corrective action. And (ii) to address the residual vulnerabilities in the information system. Web the plan of action and milestones (poa&m) is one of three key documents in the security authorization package and describes the specific tasks that are planned: Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories. Sensitive descriptions of specific weaknesses.
Sensitive descriptions of specific weaknesses. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. (i) to correct any weaknesses or deficiencies in the security controls noted during the assessment; The csp may add to the format, as necessary, to comply with its internal policies and fedramp requirements; However, csps are not permitted to alter or delete existing columns or. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m. Web date poa&m item was last changed or closed identifier specified in the inventory this is a unique string associated with the asset, it could just be ip, or any arbitrary naming scheme. Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories. Web system level it security poa&m example enclave is type: Web june 28 | 2022.
(i) to correct any weaknesses or deficiencies in the security controls noted during the assessment; Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m. Web system level it security poa&m example enclave is type: Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf of the program office or the dod component. And (ii) to address the residual vulnerabilities in the information system. The csp may add to the format, as necessary, to comply with its internal policies and fedramp requirements; Web june 28 | 2022. Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective action and implement/test the corrective action.
PPT POA&M PowerPoint Presentation, free download ID3204262
Web june 28 | 2022. Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. However, csps are not permitted to alter or delete existing columns or. Describe security weaknesses identified during certification or by the.
Poam Army Army Military
(i) to correct any weaknesses or deficiencies in the security controls noted during the assessment; Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. Web system level it security poa&m example enclave is type: Web june 28 | 2022. However, csps are not permitted to alter or delete existing columns.
Poa&M Template Dod Flyer Template
Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m. The csp may add to the format, as necessary, to comply with its internal policies and fedramp requirements; Web date poa&m item.
Material Takeoff Template Template 1 Resume Examples RXk87Zl3ZW
Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective action and implement/test the corrective action. Web the plan of action and milestones (poa&m) is one of three key documents in the security authorization package and describes the specific tasks that are planned: Be.
NIST 800171 System Security Plan (SSP) & Plan of Action & Milestones
Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories. Web the fedramp poa&m template provides the required information presentation format for preparing and.
Download New Smart Business Plan Template can save at New Smart
And (ii) to address the residual vulnerabilities in the information system. However, csps are not permitted to alter or delete existing columns or. Web the plan of action and milestones (poa&m) is one of three key documents in the security authorization package and describes the specific tasks that are planned: Fedramp updated the plan of actions and milestones (poa&m) template.
Free Project Milestone Templates Smartsheet
Web system level it security poa&m example enclave is type: Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories. Sensitive descriptions of specific.
Stock Count Excel Spreadsheet with regard to Small Business Inventory
However, csps are not permitted to alter or delete existing columns or. Web the plan of action and milestones (poa&m) is one of three key documents in the security authorization package and describes the specific tasks that are planned: Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done.
Plan Operativo Anual INEM 2020 Google Sheets
Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf of the program office or the dod component. Fedramp updated the plan of actions and milestones.
PPT ODAA PowerPoint Presentation ID6519667
Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Web system level it security poa&m example enclave is type: Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf of the program office or the dod component. However, csps.
The Csp May Add To The Format, As Necessary, To Comply With Its Internal Policies And Fedramp Requirements;
Web key concepts the oscal plan of action and milestones (poa&m) model is part of the oscal assessment layer. Describe security weaknesses identified during certification or by the annual program review, independent evaluations by igs, or any other work done by or on behalf of the program office or the dod component. Fedramp updated the plan of actions and milestones (poa&m) template to include two new columns. Web the project plan in ms excel format, sometimes called a plan of actions and milestones (poam), uses a method of planning called raci that designates who is responsible, accountable, consulted, and informed about each task by assigning people (by name) for each of these categories.
Web Date Poa&M Item Was Last Changed Or Closed Identifier Specified In The Inventory This Is A Unique String Associated With The Asset, It Could Just Be Ip, Or Any Arbitrary Naming Scheme.
However, csps are not permitted to alter or delete existing columns or. Web june 28 | 2022. Be sure to include the total funding requirements in the security costs field in column 13 of the poa&m. Web the plan of action and milestones (poa&m) is one of three key documents in the security authorization package and describes the specific tasks that are planned:
Web System Level It Security Poa&M Example Enclave Is Type:
And (ii) to address the residual vulnerabilities in the information system. Completion dates shall be determined based on a realistic estimate of the amount of time it will take to procure/allocate the resources required for the corrective action and implement/test the corrective action. Web the fedramp poa&m template provides the required information presentation format for preparing and maintaining a poa&m for the system. (i) to correct any weaknesses or deficiencies in the security controls noted during the assessment;